Before getting into the security aspect of APIs, let's talk about what they are, and why are we talking about that?
What are APIs?
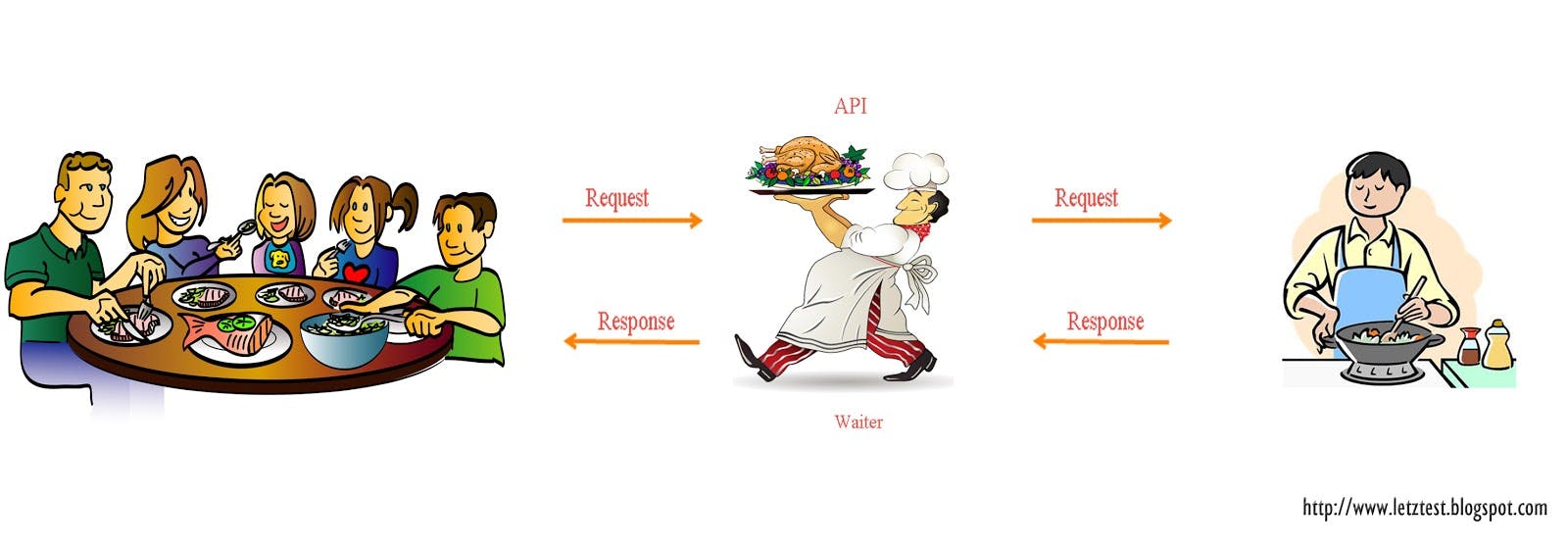
An API is the messenger that takes requests and tells a system what you want to do, and then returns the response back to you. Think of it like a waiter in a Hotel, He/She receives the requests from you, gets back into the kitchen section and then brings the dish for you post cooking. One of the visuals will help you understand better about the role of APIs.
Why APIs matter?
APIs are everywhere. APIs are the engine under the hood because of which we are living in a connected world.
Swagger and OpenAPI ( Where's the confustion?)
The API specification was developed by a company called smartbear and later it was donated to openAPI which comes under the umbrella of Linux Foundation. openAPI is a standard that defines how we define our APIs. Since, this is a standard of defining APIs, we have many tools built around it. Swagger editor is one of the tool that we will be checking out later in the blog. So to summarize swagger is a tool and openAPI is the specification
Why openAPI specification?
One of the question that you might be having in your head is that why one would use openAPI specification and why not directly develop the API? It's language agnostic, so it's easier for anyone to get familiar with the API without any barrier of having knowledge about a language. There are many tools around openAPI spec, so you can leverage that to develop your APIs pretty fast. You can use tools for document generation, testing and validating your APIs. With openAPI we can develop a prototype of the API before implementing it and that's useful in order to get feedback on the API that we are going to build.
Take a break, We have covered the basics of APIs, and now we are entering into the zone where we will talk about the security aspect of APIs.
API security
Introduction to CherryBomb
Just like we have many tools out there that simplifies the generation of YAML manifests when it comes to kubernetes. Similarly, We have a bunch of tools that simplifies the genration, testing and documentation of APIs. Cherrybomb is one of the tool that is developed by BLST security.
Lab Section
- In this, I will be writing a openAPI spec for the books API. We can fetch the book details with the API and simultaneously.
openapi: 3.0.1
info:
title: Books API
description: A simple API which gives you info related to books
version: 1.0.1
contact:
name: library
url: demo-example.com
servers:
- url: https://booksapi.com
paths:
/book:
description: Book Resource
get:
description: Opeartion to fetch Book details
parameters:
- in: query
name: bookName
required: true
schema:
type: string
example: Jake
responses:
200:
description: success response
content:
application/json:
schema:
$ref: '#/components/schemas/books'
post:
description: Add a new book
requestBody:
content:
application/json:
schema:
$ref: '#/components/schemas/book'
responses:
201:
description: record successfully added
/book{id}:
description: get student based on path parameter
get:
parameters:
- in: path
name: id
required: true
schema:
type: integer
responses:
200:
description: successful response with path Parameter
content:
application/json:
schema:
type: object
properties:
studentID:
type: integer
example: 3
studentName:
type: string
example: David
studentRemarks:
type: string
example: High Grade student
components:
schemas:
book:
type: object
properties:
studentID:
type: integer
example: 3
studentName:
type: string
example: David
studentRemarks:
type: string
example: High Grade student
books:
type: object
properties:
studentID:
type: integer
example: 3
studentName:
type: string
example: David
studentRemarks:
type: string
example: High Grade student
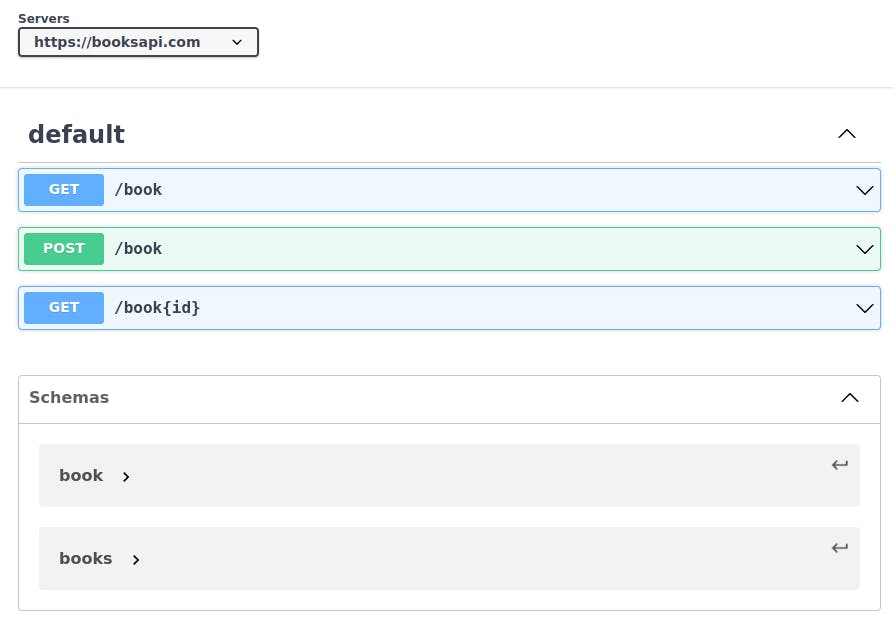
- If you'll look at the swagger editor, then the API will look something like this.
- Now, we have written one sample API. It's time to test the same with cherrybomb.
- First we will test the API with the CLI, then we will use the GUI.
Install cherrybomb & verify the installation
curl https://cherrybomb.blstsecurity.com/install | /bin/bash
cherrybomb --version
After finishing the installation, let's try out cherrybomb. Write your openAPI spec in your system and recall the path of the file.
Execute the following command
cherrybomb oas --file <path-to-your-file>
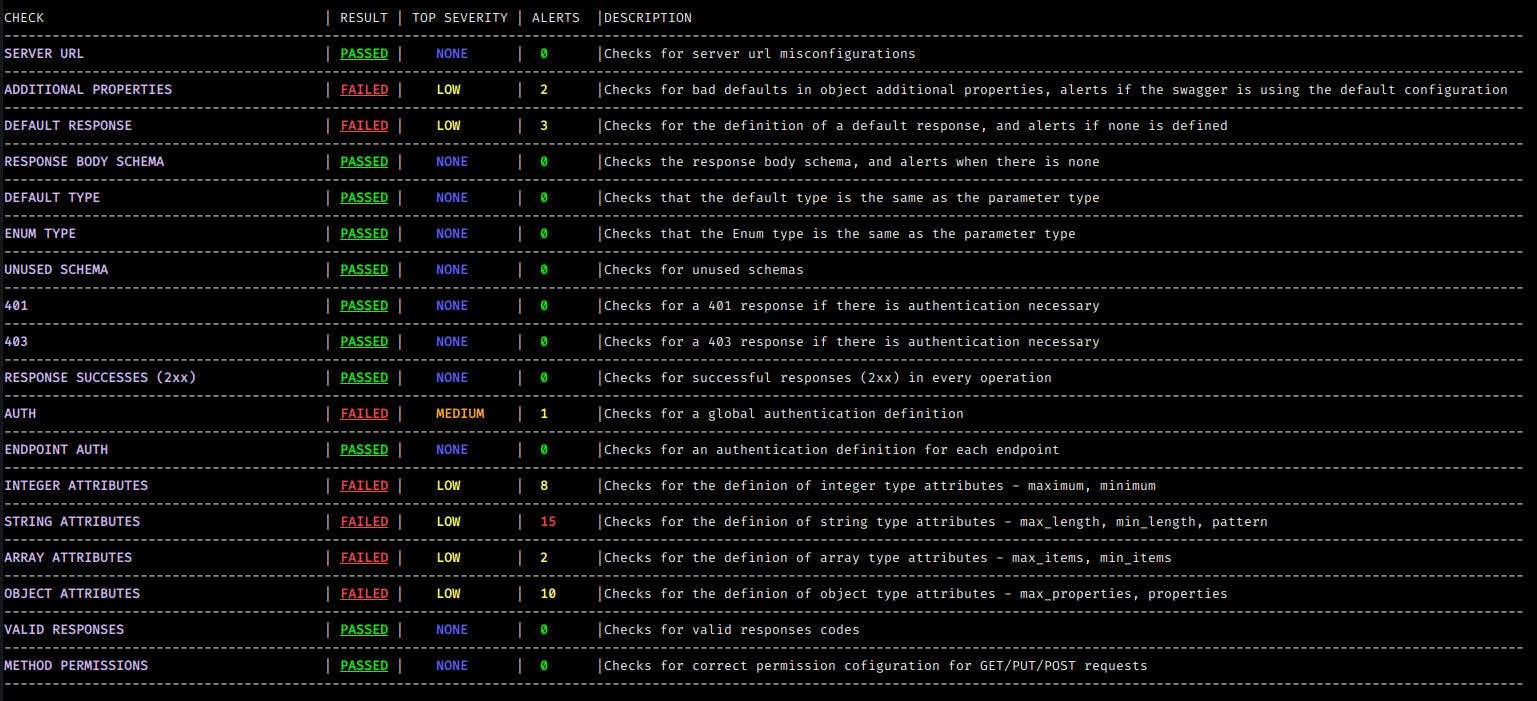
You will notice that cherrybomb gives you the result of your API spec based on several parameters. You can use this and improve your API spec before implementation of the API.
Furthermore, you can have a look at the endpoints of your API spec using the command
cherrybomb ep-table --file <path-to-your-file>
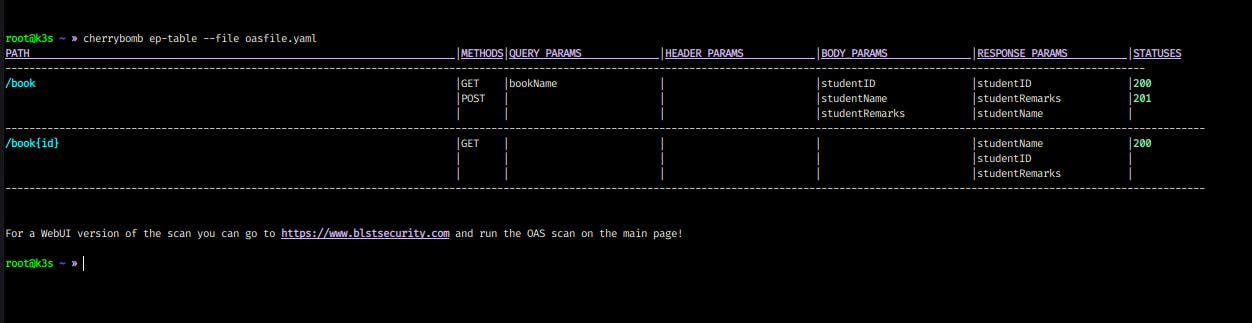
Cherrybomb works perfect on the CLI, but one problem I faced is because of my hardware. If you using a small screen laptop like me then you have to adjust the size again and again and it can be frustrating at times. If you've large screen then it will work perfect.
One possible solution for this is to use the web UI that is provided by BLST security. Let's explore that.
You first need to signup here After signing up, you will see the dashboard and here you need to upload your openAPI spec file.
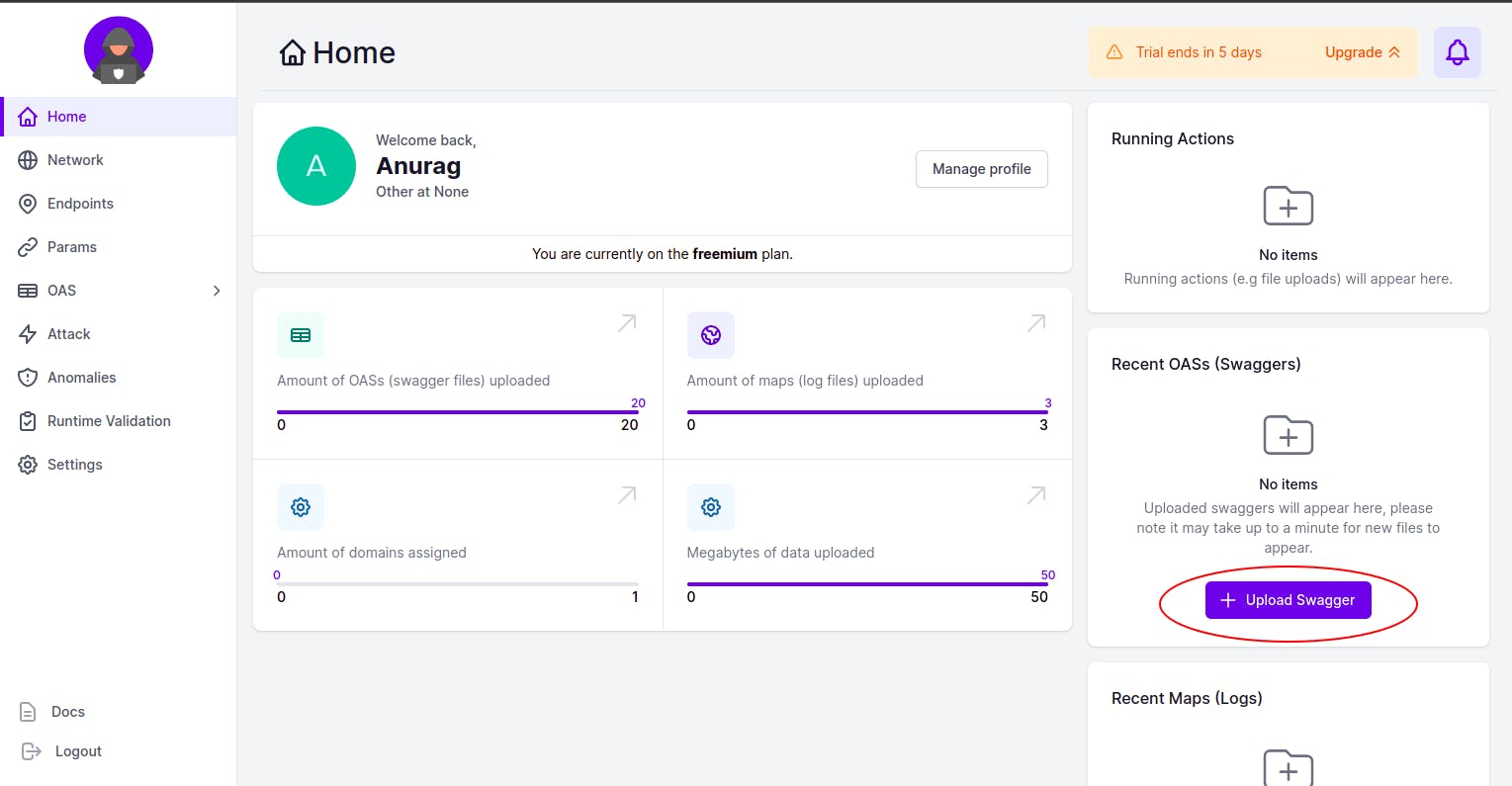
After uploading, you will see that the actions are running in the background and your results will be visible to you in the UI soon.
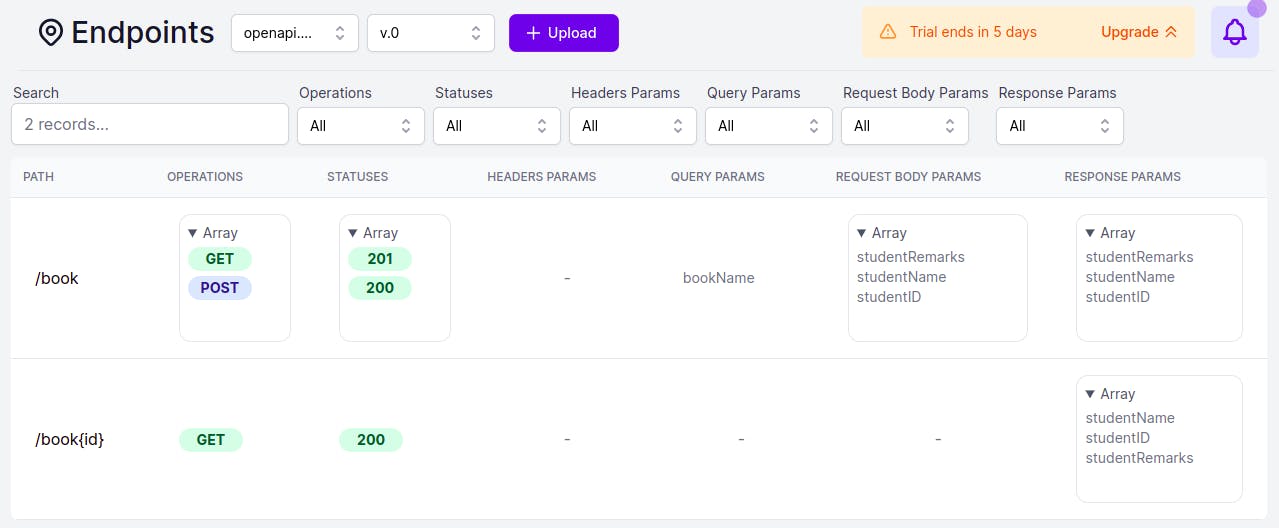
You can visualize all the endpoints, and for me, it's better than the CLI.
You can look at the summary of your API spec under the summary tab.
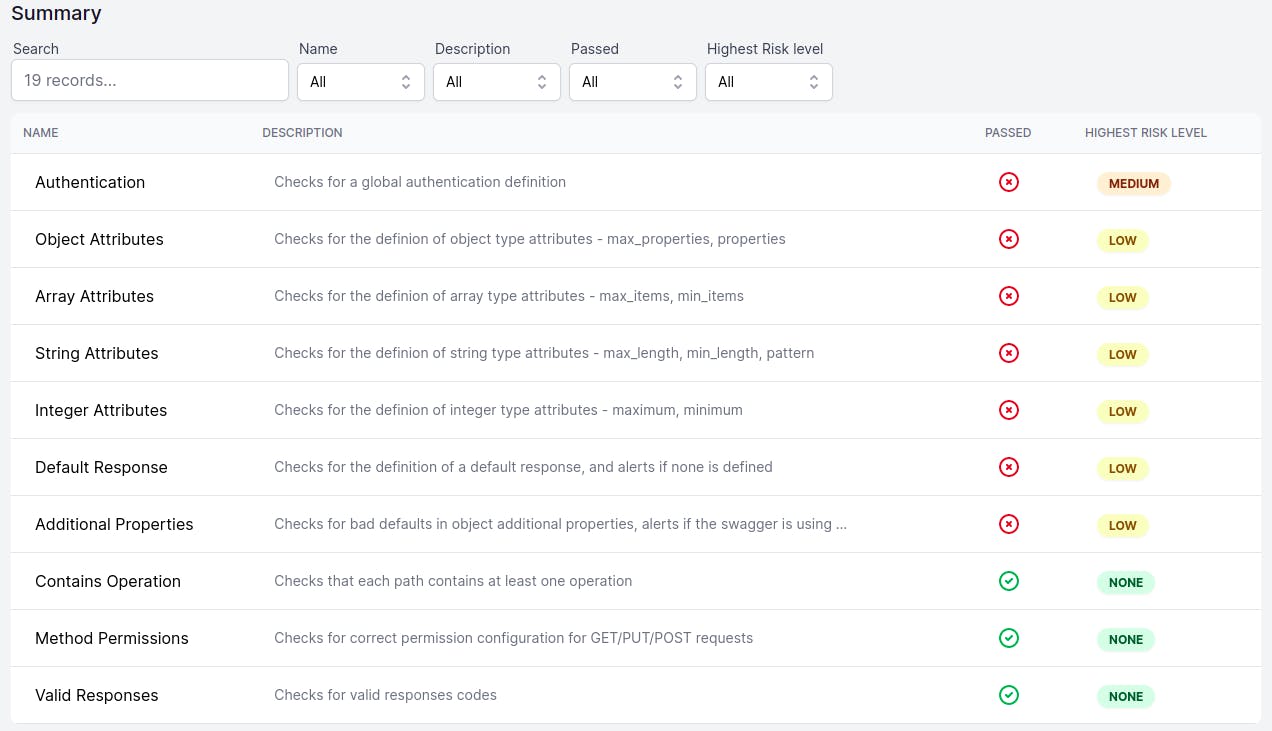
There are several parameters on which you can evaluate your API spec in the browser UI, and it looks great. You can query your API on a number of parameters.
Thank you for Reading. Please reach out if you want to suggest any improvement.