Agenda
- Introduction to Kubescape & Installation
- Scanning k8s cluster,YAML manifests and helm charts
- RBAC visualizer
- VScode extension
- Github actions with Kubescape
- Using GitOps With ArgoCD
- How Kubescape works under the hood
Introduction to Kubescape
- Security is generally hard and when it comes to security in a distributed system it becomes even more harder.
- It is getting more and more complex with time. Kubescape is the open source project by ARMO which solves this problem. Although it's important to mention that absolute security is not possible, we can try our best to minimize the risk and hence damage caused.
Why even bother about security?
- Going through this article you'll notice that most of the images are having security vulnerabilities. In k8s there are many loopholes that can be used against you.
What is kubescape?
- Kubescape is a kubernetes security tool by ARMO. ARMO is a company which is focusing heavily on the security side of k8s.
- ARMO mainly focuses on DevSecOps
- Kubescape is a security tool testing kubernetes security.
- Kubescape provides single pane of glass for:
- Risk analysis
- Security compliance
- RBAC visualizer
- image vulnerabilities scanning
- Early vulnerabilities scanning in your CI/CD pipeline
Installation of kubescape just takes one command.
curl -s https://raw.githubusercontent.com/armosec/kubescape/master/install.sh | /bin/bash
- To verify the installation of kubescape you can use
kubescape version
What kubescape scans?
- It scans kubernetes cluster
- It scans your yaml manifests
- It also scans your helm charts
- Here I'm putting a recording in which first I scan my kubernetes cluster then a k8s deployment manifest and finally a helm chart.
So, You have seen that scanning your cluster, charts and manifests is easy with kubescape. Let's get our hands dirty and try to fix any issue with the pod that we have created. In the last pod we have not mentioned liveness probe and so we need to mention that in the pod manifest and we will notice that it's not showing the same error anymore. After adding liveness probe our manifests will look something like this. Now we will do kubectl apply -f demopod.yaml and we have fixed a misconfiguration with the help of kubescape.
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
run: nginx
name: nginx
spec:
containers:
- image: nginx
name: nginx
resources: {}
livenessProbe:
exec:
command:
- cat
- /tmp/healthy
initialDelaySeconds: 5
periodSeconds: 5
dnsPolicy: ClusterFirst
restartPolicy: Always
status: {}
What kubescape offers?
- With kubescape you can detect misconfigurations according to multiple frameworks such as NSA, MITRE, Devops Best etc. You can also create your own framework.
- Recent survey shows that 51% of the images have vulnerabilities within them and using kubescape you can scan container images for vulnerabilities. Not only scanning you can also see the severity of vulnerabilities with kubescape and the images that are most vulnerable (critical in kubescape terms), you can fix that first.
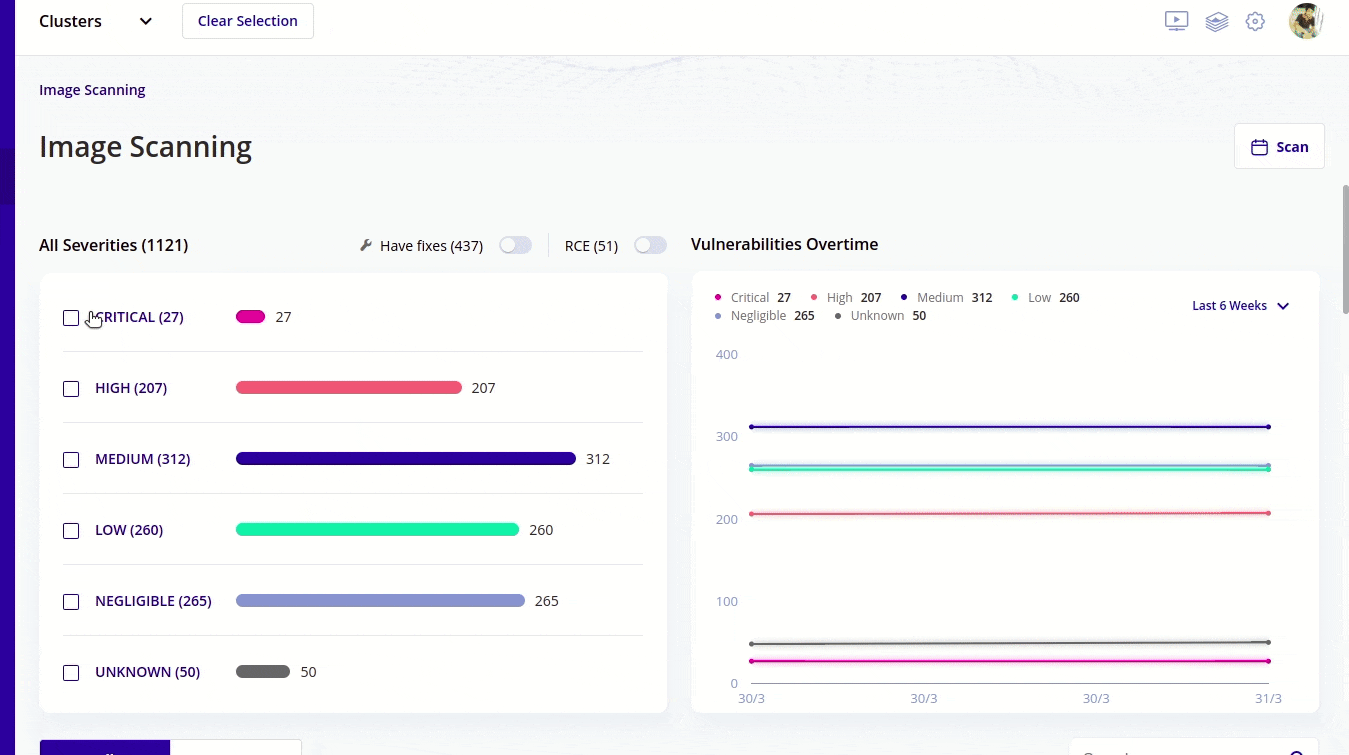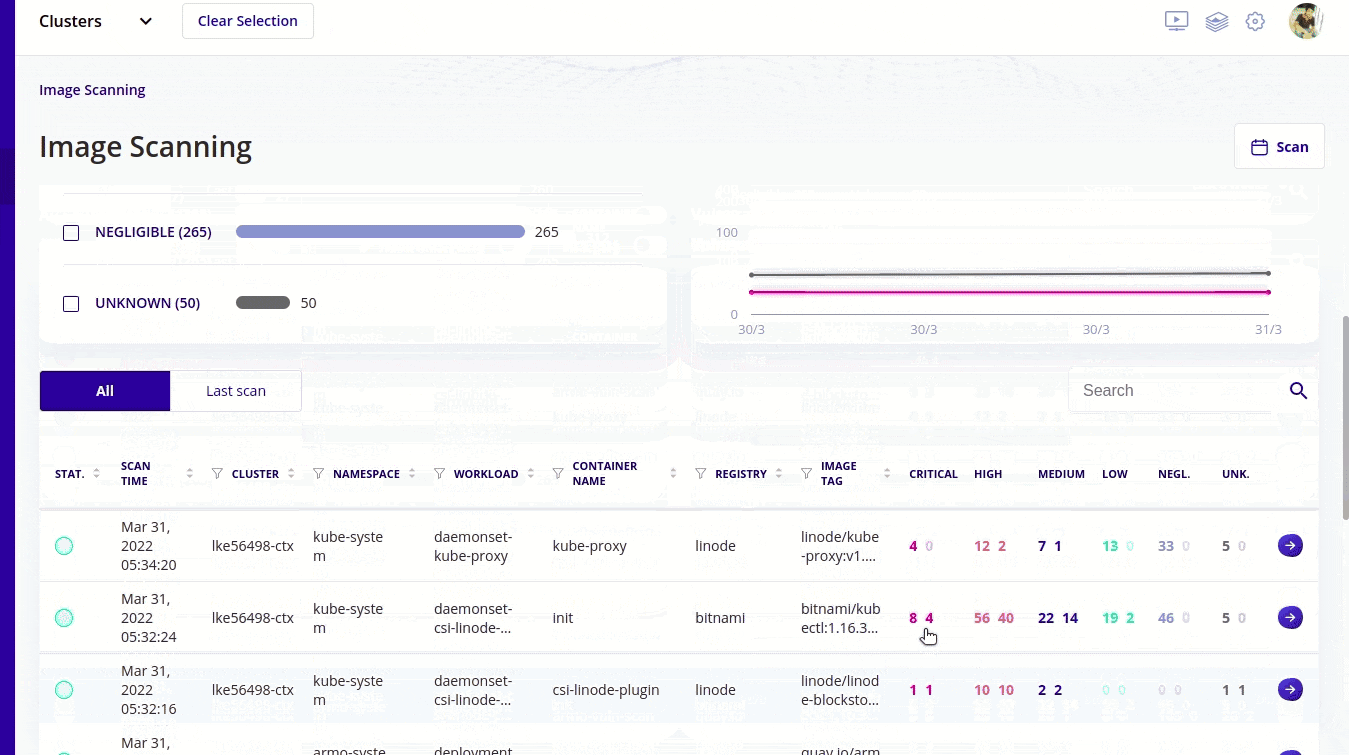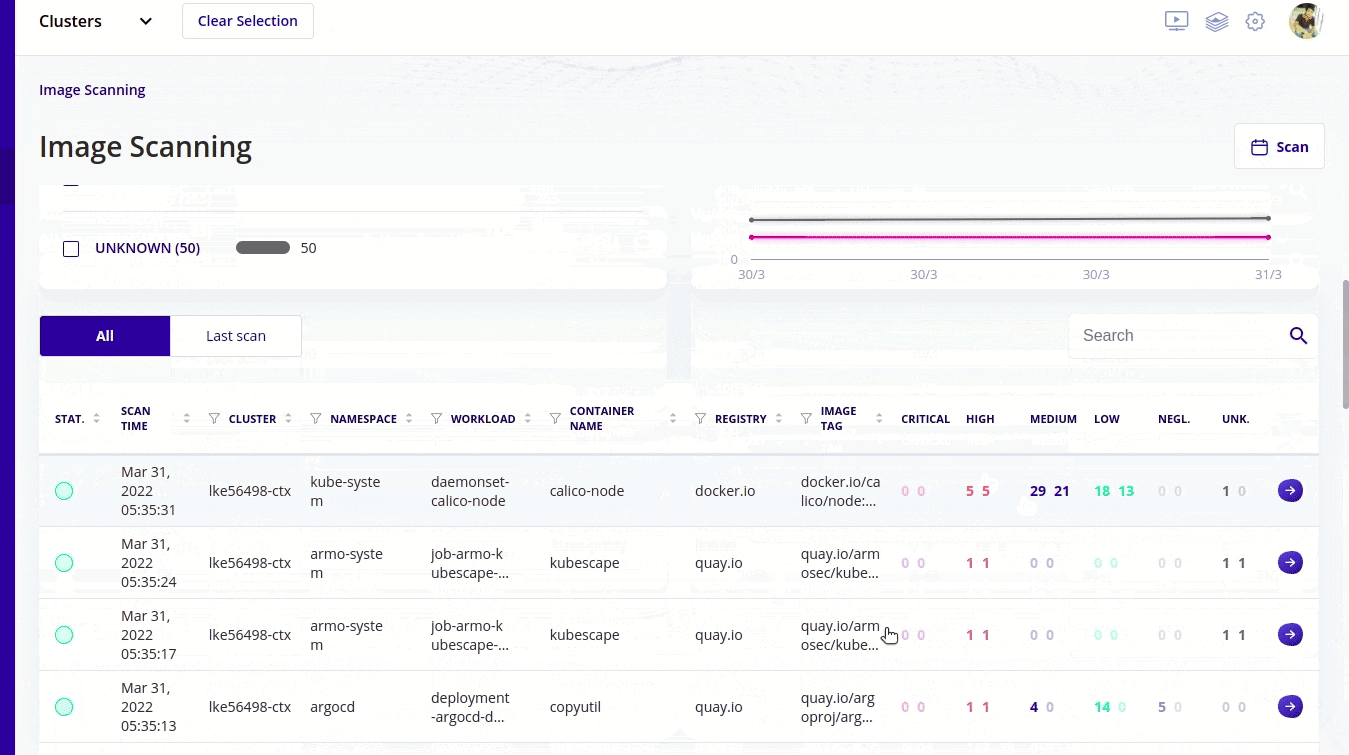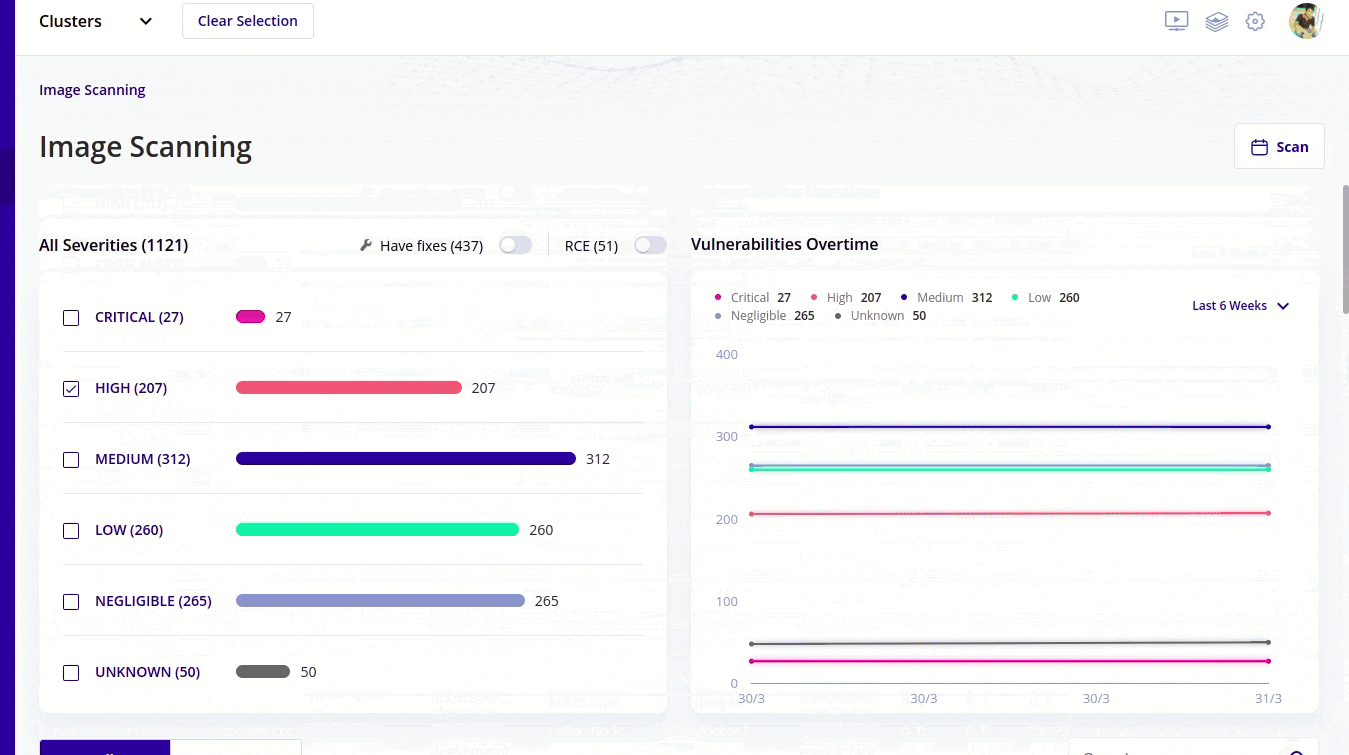
- When you start with RBAC in the starting it seems an easy thing to handle but very soon you realize that it's getting complex. As your organisation grows in size you see that RBAC becomes tough to manage. Kubescape simplifies this with easy to understand and easy to visualize graphical user interface. I will talk about it after sometime.
What is the framework?
- A framework consists of multiple controls(tests). Framework is like a security standard set by some organisations/individuals to secure your organisation from security breach and attacks. It is a standard to secure your kubernetes cluster. Some of the popular frameworks out there are [NSA-CISA], MITRE
- What is scan-risk score?
kubescape scan framework nsa --fail-threshold 0It basically says that if there's anything wrong then stop everything and let the user fix that first. It simply states that I love my cluster and I don't want a single vulnerabilities in my cluster. 100% score is the worst possible scenario.- ARMO also has its own ArmoBest framework. ARMO continuously keeps on upgrading this framework as and when the latest vulnerability comes to notice. Whenever any latest security breach happens in the industry armo tries to update it as soon as possible.
- Although we can check the output of what vulnerabilities we're having in our cluster within our terminal, you'll see that very often the list is huge. It becomes very difficult to fix your vulnerabilities via the command line. Thus we all use Armo web portal.
- Whatever controllers they have in the framework you will most certainly not require those all. If you'll use the popular frameworks like NSA, MITRE then you'll probably never be able to get a 100% scan-risk score and this can be irritating at times because you want perfection.
- Reason for custom framework is that you can customize the framework according to your need or according to the need of your organisation.
- The NSA, MITRE and devops best practices are humongous and this can be overwhelming for you and this can be another reason why you should consider your own framework?
Creating your own custom framework is easy
- Go to this path and select new framework and then select the controls that you think is vital for you or your organisation.
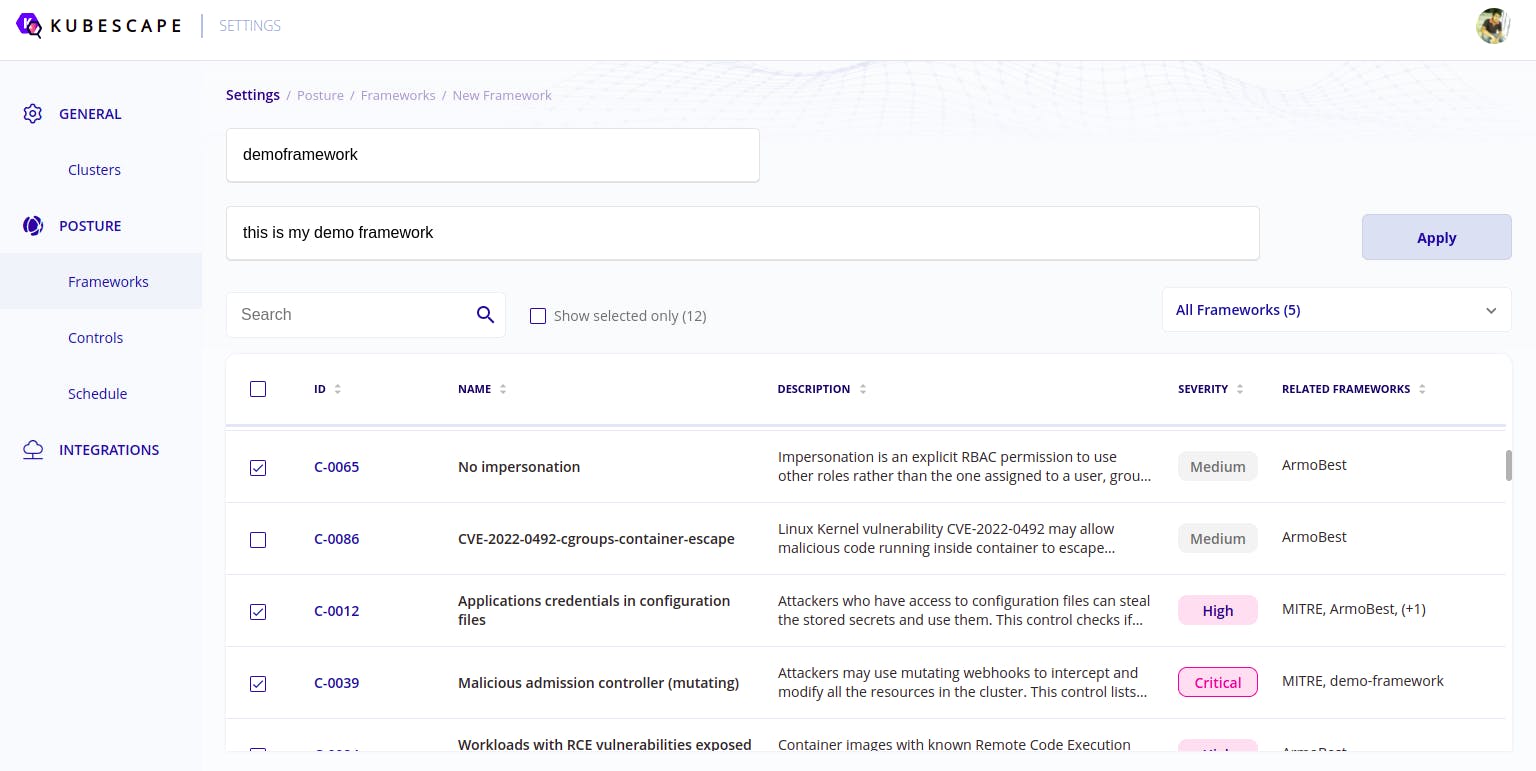
Enabling exception
- We need it because many times what happens is that we know prior to running the scan that something is vulnerable and we accept the risk related to it. It may be that we are using an old version of a k8s component or something is deprecated and we are still waiting for the new release. In this case we can tell kubescape that I need this thing to be an exception.
- Kubescape will not consider this parameter while calculating the risk score and yes will not get irritated too by getting the same security control popping on your screen again and again. We can create exceptions for a particular namespace or a given workload in kubernetes.
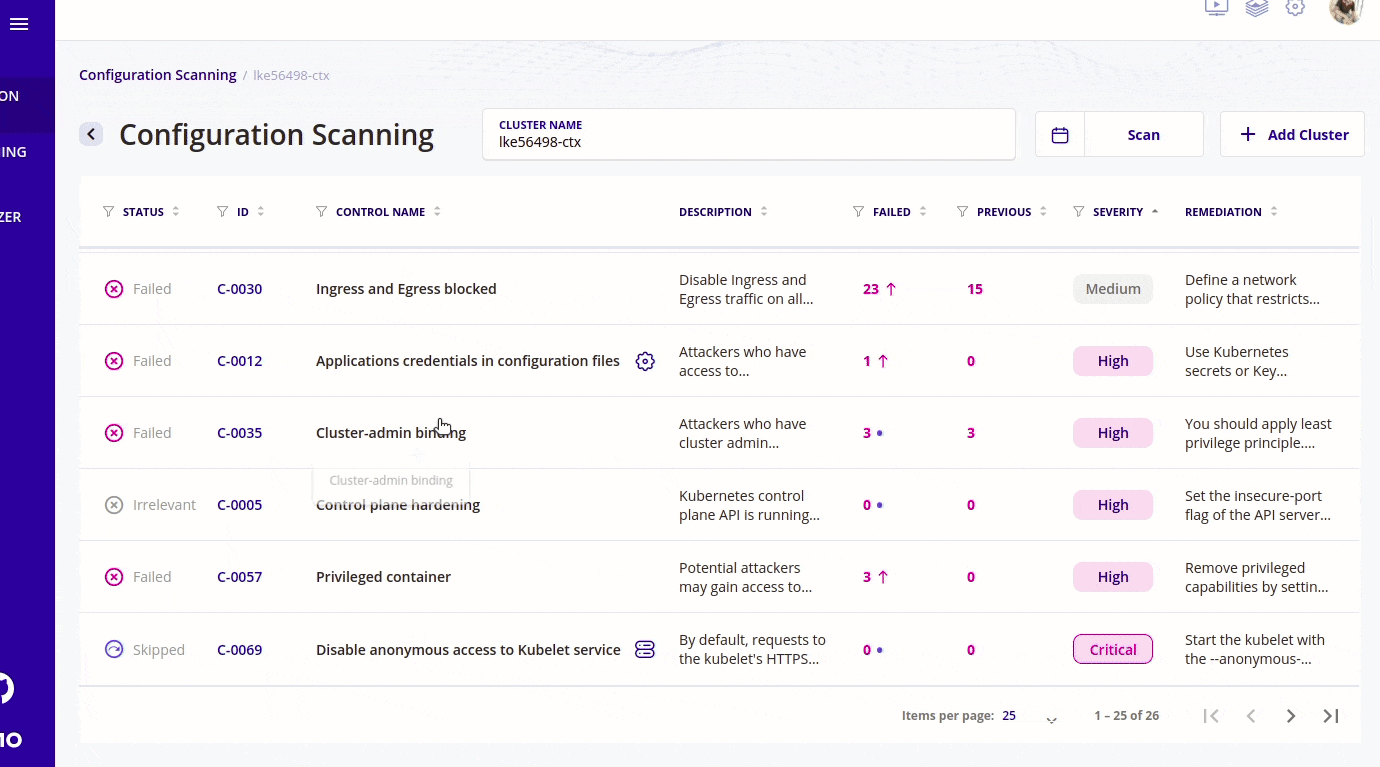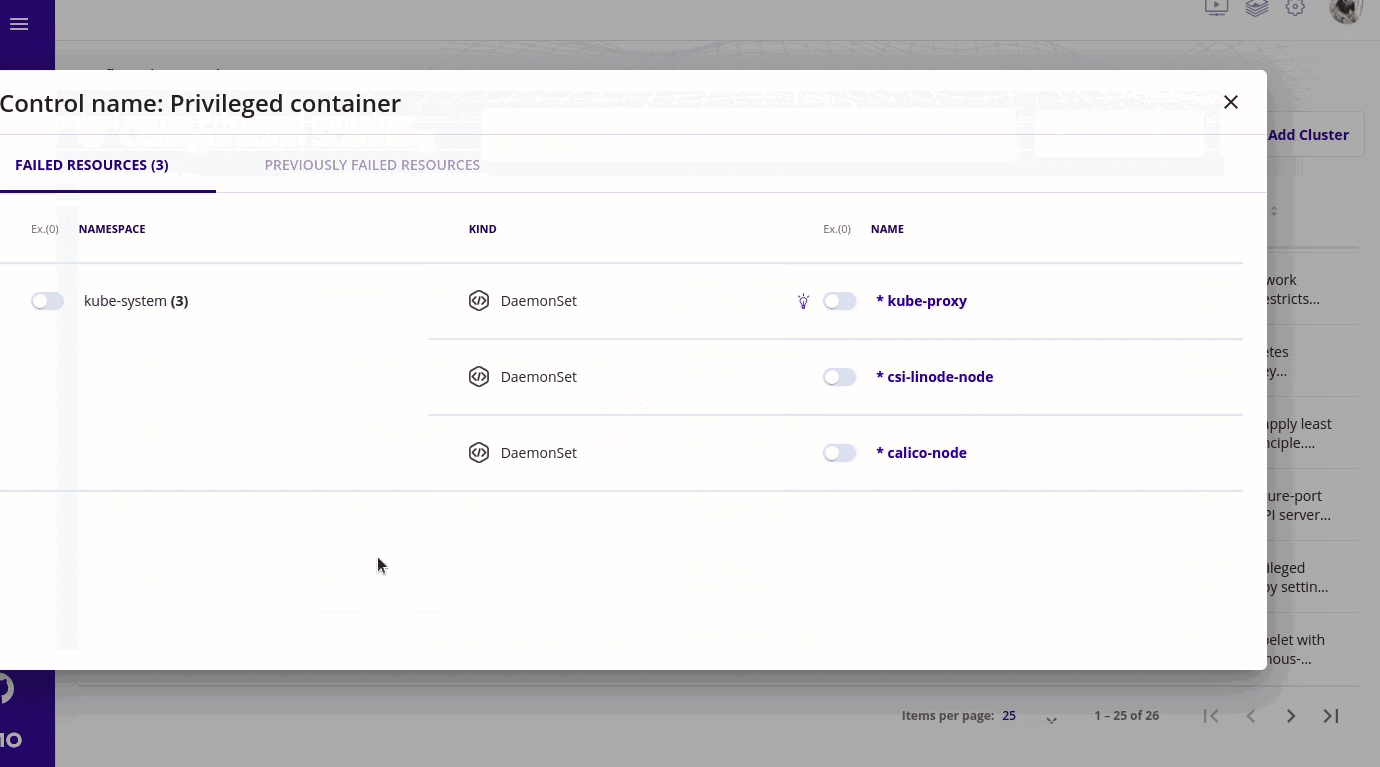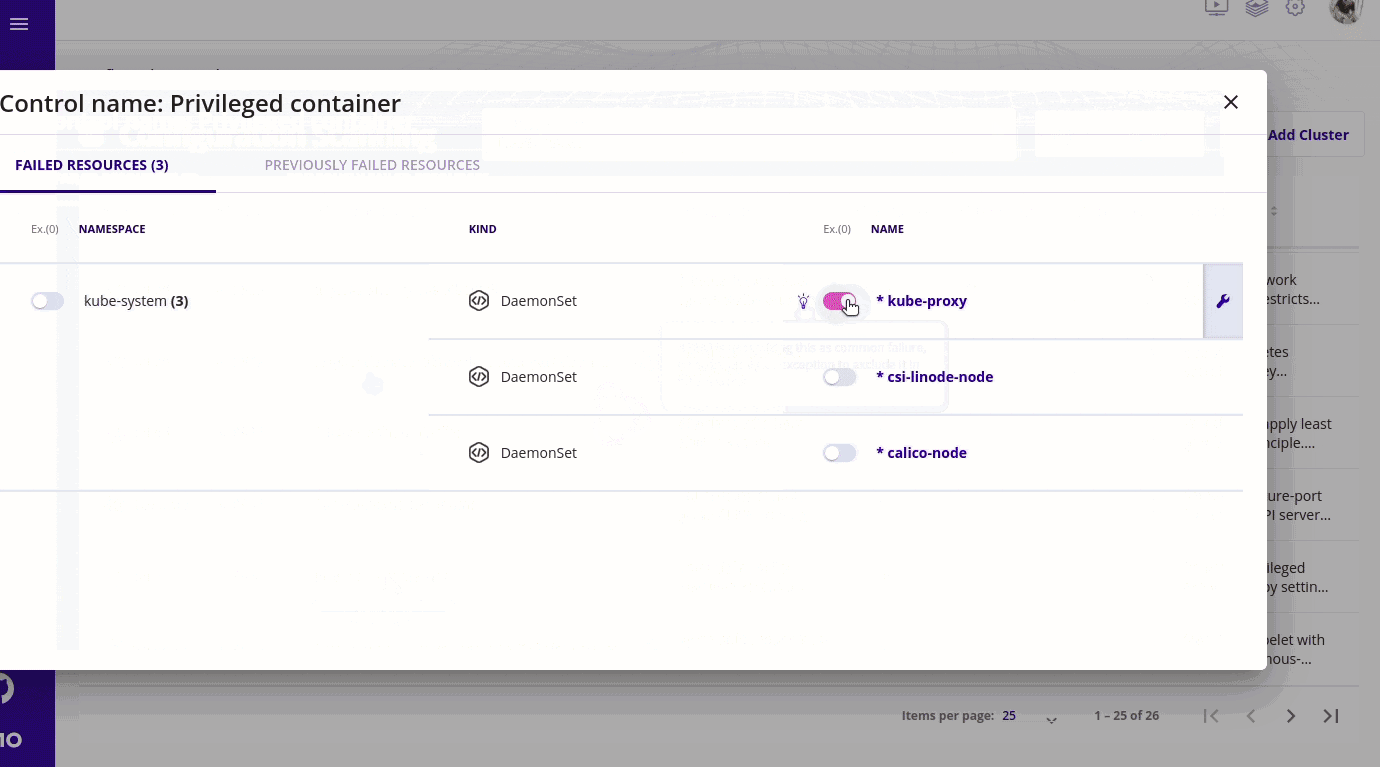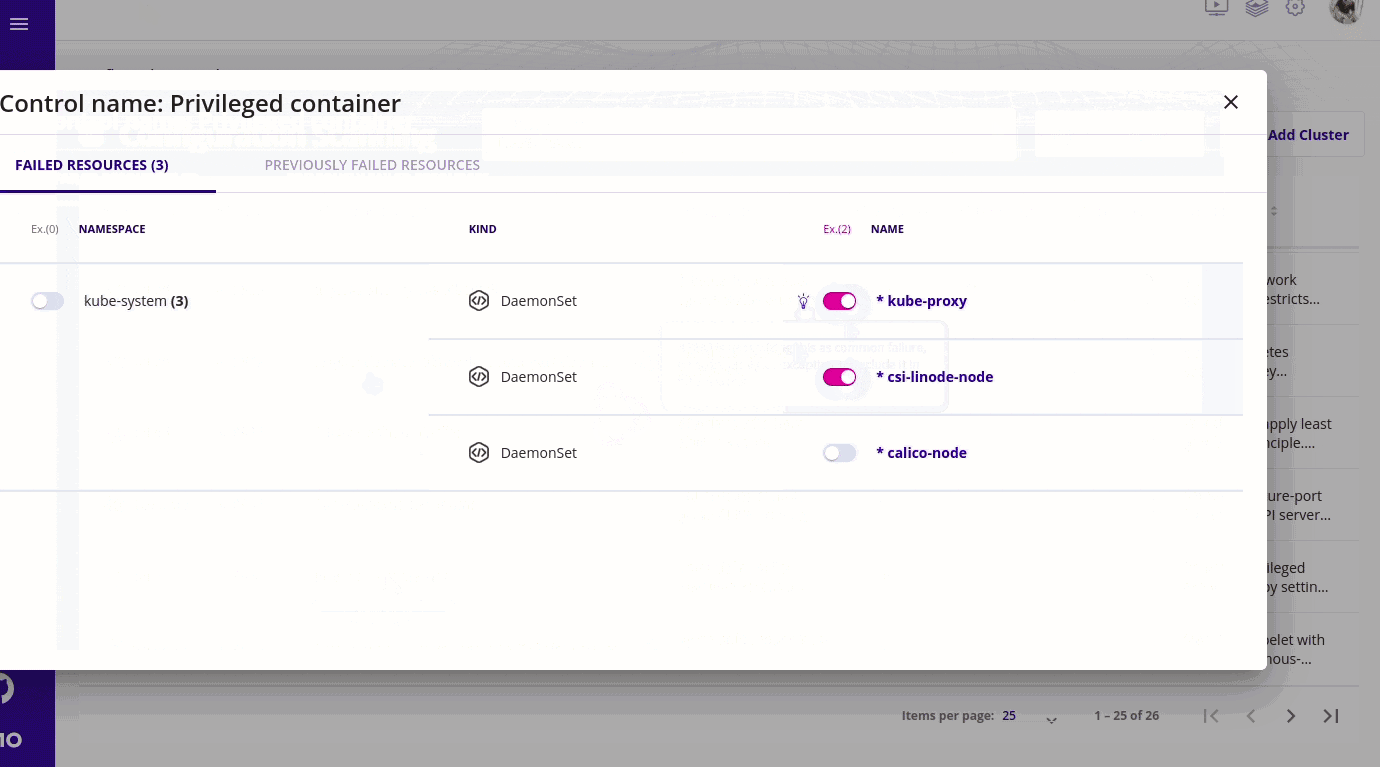
RBAC visualizer
- I will quickly try to explain why we need RBAC in kubernetes? The example that I frequently discuss with my friends is that suppose someone has joined a company and he/she gets frustrated by anything and then starts playing with the cluster and starts deleting resources. The reason for frustration can be anything. Also it is important with respect to security as well. You don't want everyone to have access to your secrets.
- With RBAC visualizer we can also check who has access to what resources. Like if we want to check who has access to the secret resource then we can check that using the RBAC visualizer.
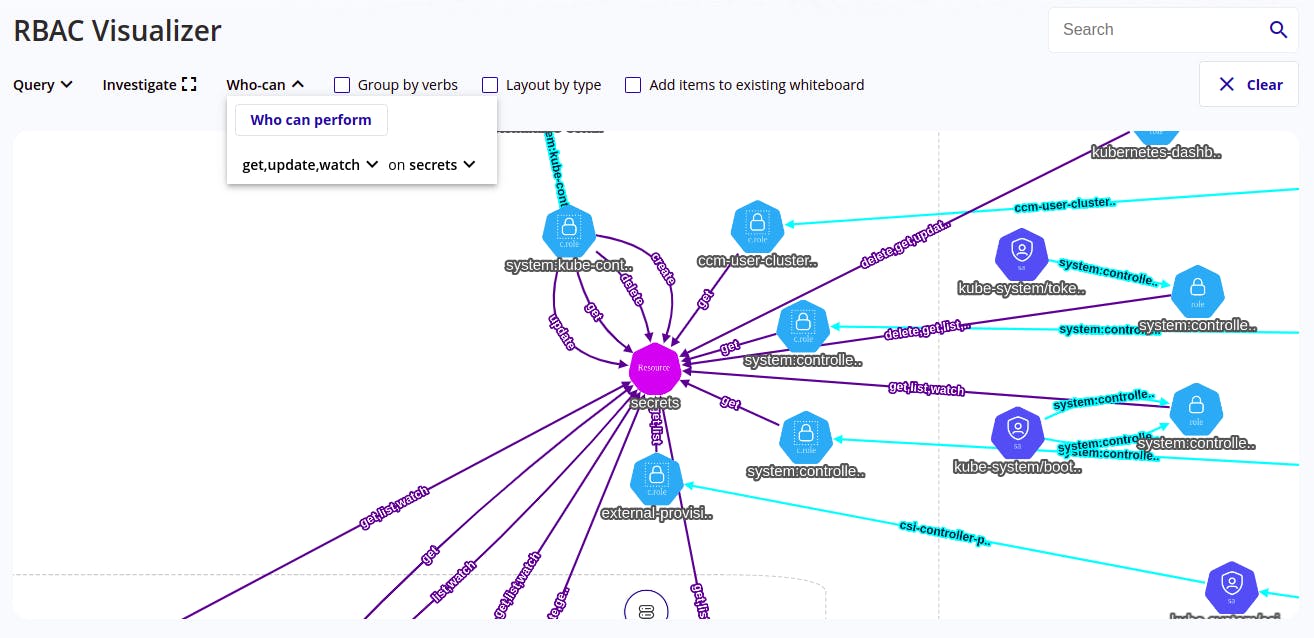
- With RBAC visualizer we can also check who can do what by running a query from the web UI itself. For example if we want to check who can exec into a pod then we can run a query based on that and kubescape will show you the results in a nice visual way. We can also check who can access the kubernetes dashboard.
- The image below runs a search on who can watch and get secrets.
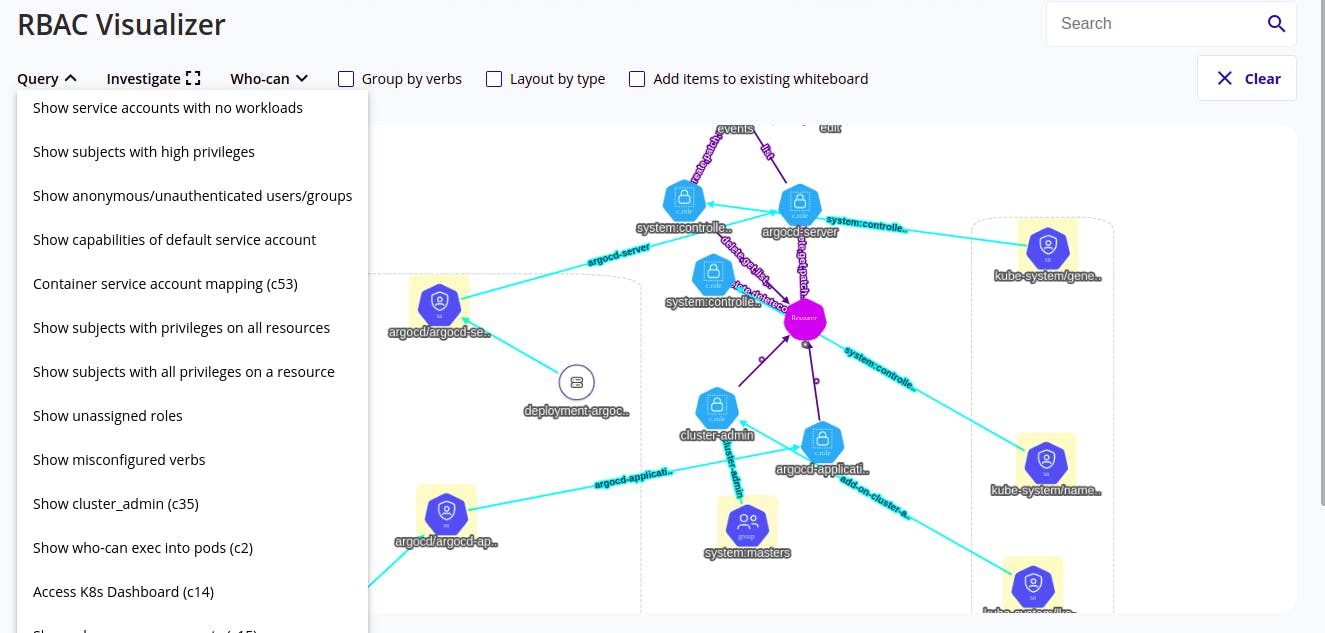
- One can also run the query from the web interface.
VSCODE kubescape extension
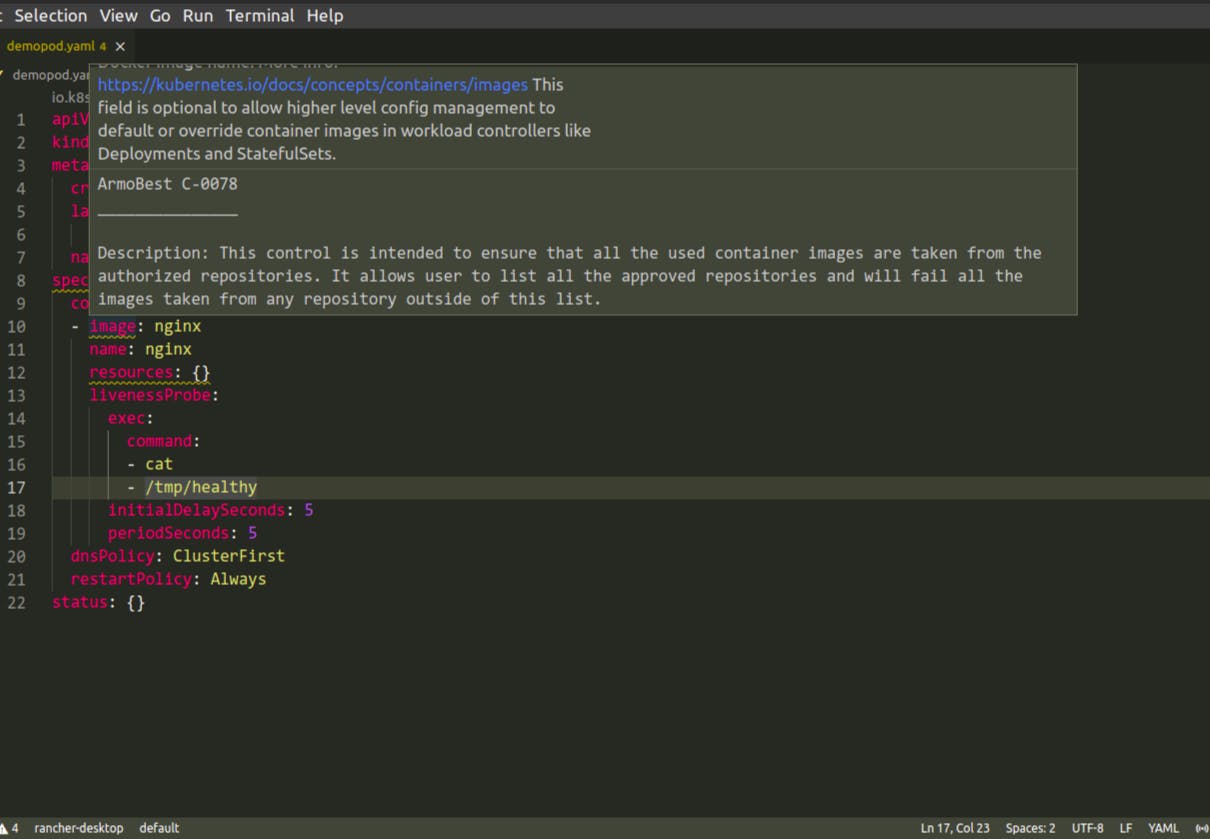
- Kubescape provides vscode extension. It will highlight the security issues when you will write the YAML manifest in the vscode editor.
- With the vscode extension we can see what is the problem with our manifests. This blog covers how to use kubescape with vscode.
Integration with CI/CD (The Gitops Way)
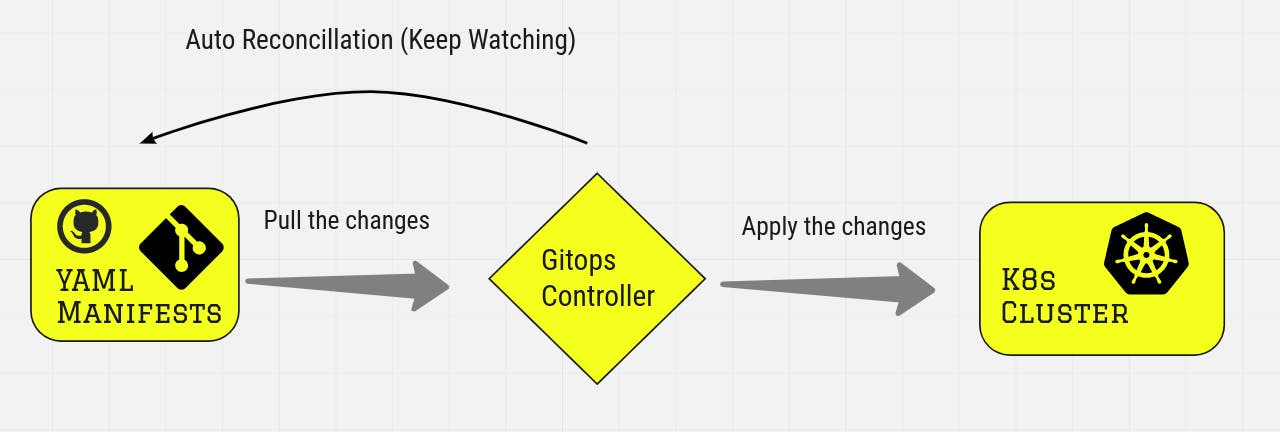
- In gitops we consider git as the single source of truth. Nothing more about gitops here. I have made a diagram that gives you a 30000 feet overview of gitops.
- In this basic demo I will be using armo risk-score to evaluate the risk in my CI/CD pipeline. I will be using github action for that. The link of the repository is here
- I hope if you're reading this then you'll implement this and get your hands dirty.
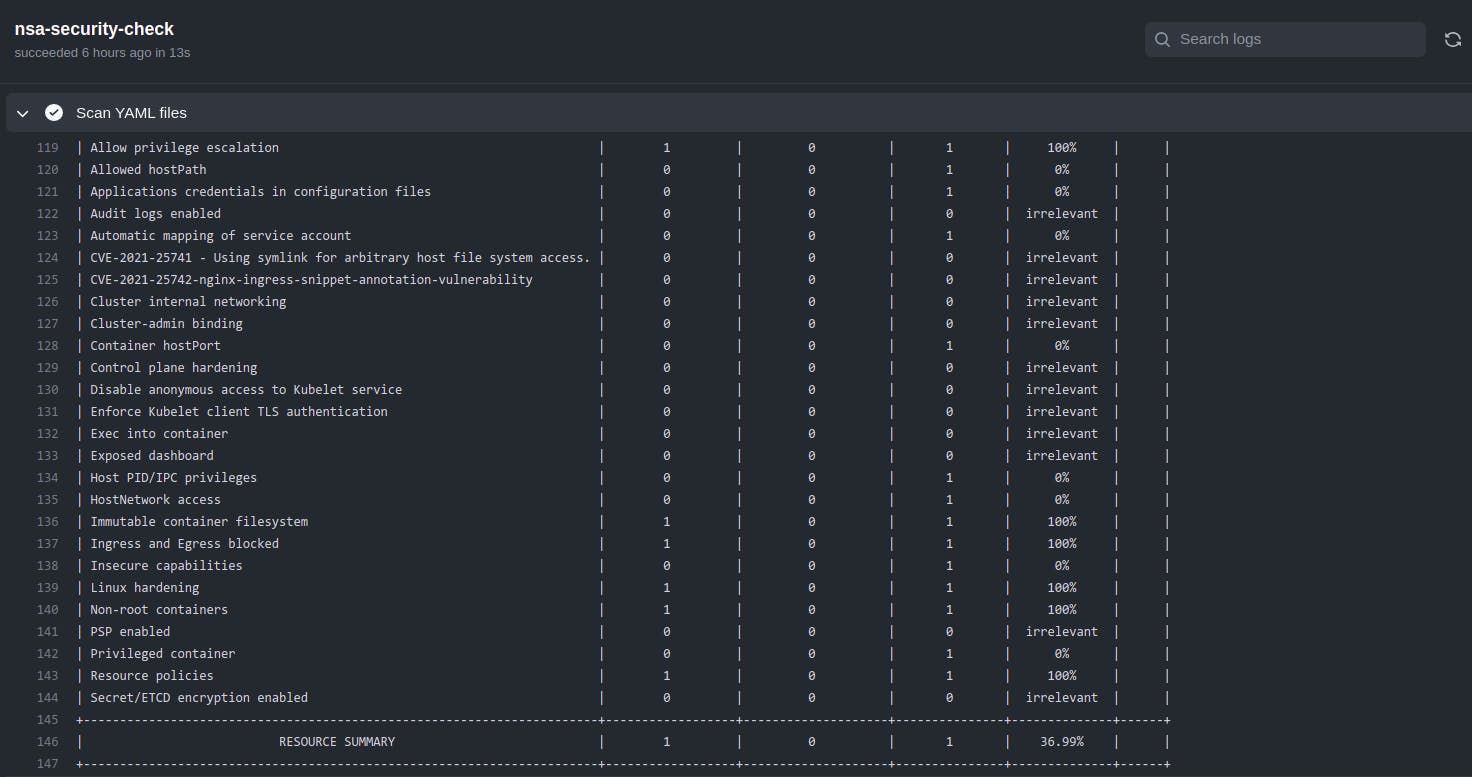
- We can check our risk score in github action. It looks something like this.
- In gitops methodology we put our YAML manifests in a git repository and we can scan that directly with kubescape. You need to run the command
kubescape scan https://github.com/kranurag7/kubescape-argo/tree/main/deployments - Now let's add our demo application to Argo using the web interface. I'm not explaining here how to setup argocd. If you need help with that then check the getting started guide.

- And the demo-app is working now. I will add a detailed README soon on github.
How to delete your cluster from kubescape UI?
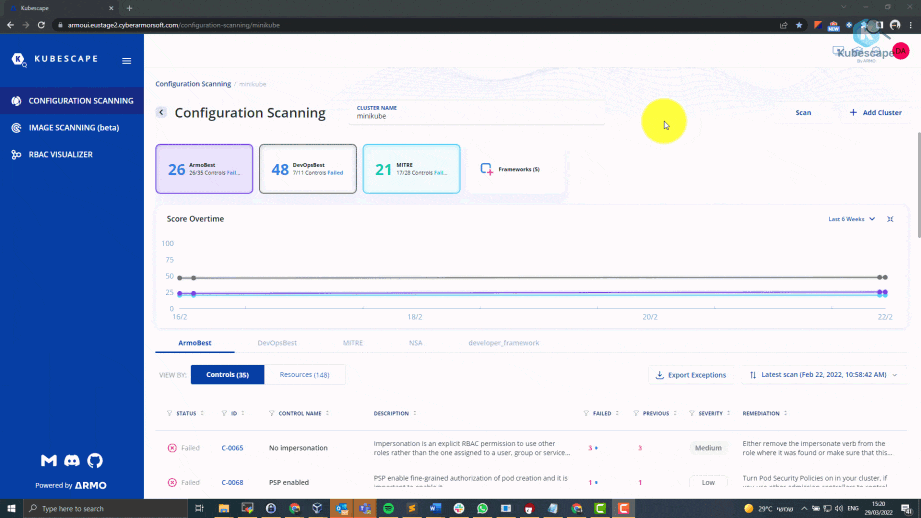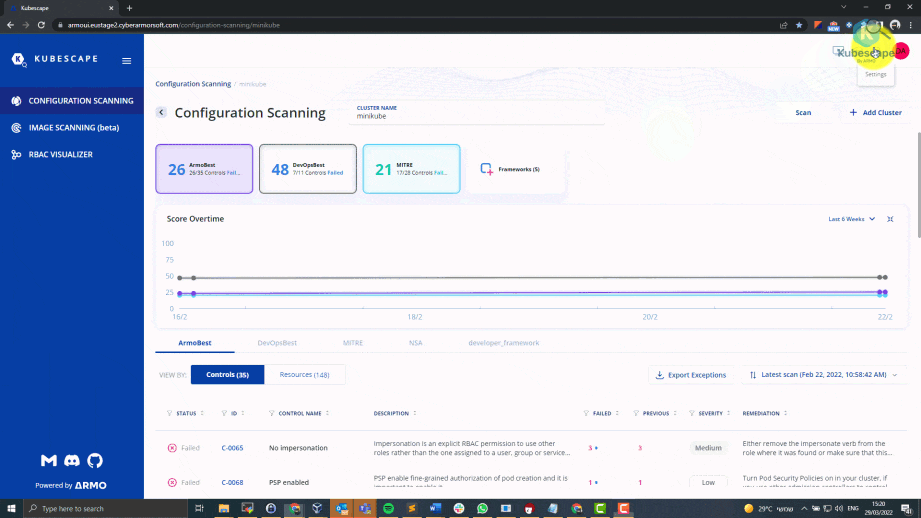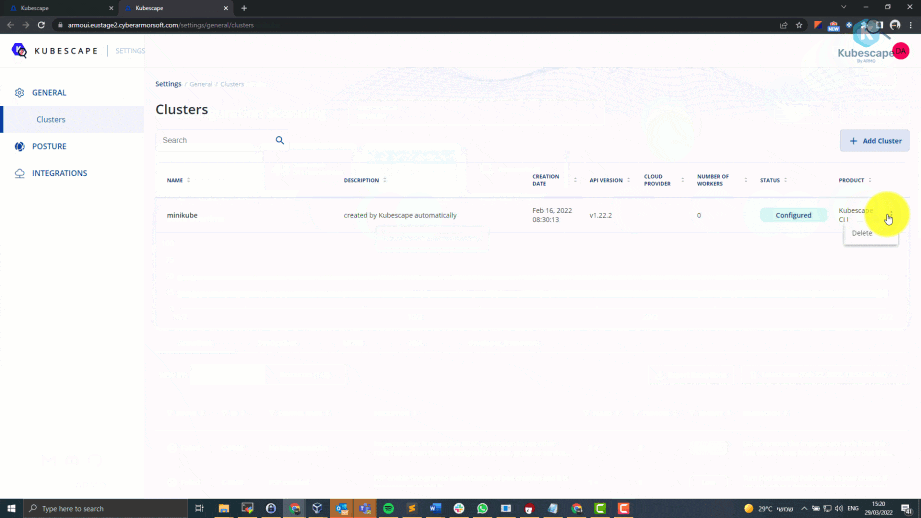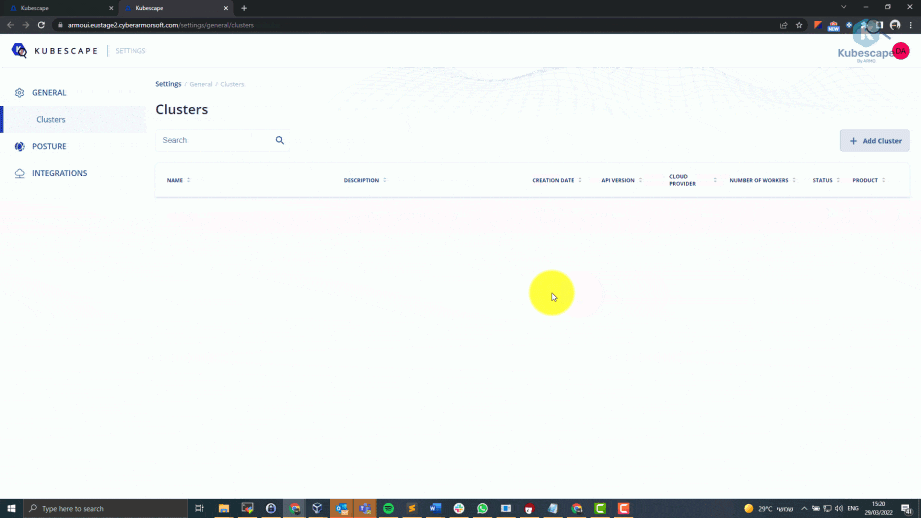
How kubescape works under the hood?
- Kubescape uses OPA to scan the possible security loopholes in your cluster,manifests and charts. If you are curious about how those things works then you can check the rego rules here. I tried understanding few examples from the rules but didn't get it. Rego is a declarative policy language developed by OPA. Kubescape retrieves information about k8s objects from api server and then it scans that with OPA.
- OPA is a general purpose policy engine which enforces policies in your kubernetes cluster.
- With OPA we can figure out:
- Can user X do operation Y on resource Z?
- What records should bob be allowed to see?
- To learn more about OPA I referred to this great article by magalix and I also played little bit with rego playground. Check this out.
Note: I will keep on updating this blog as I learn new things about the project or any other component that I have used in this article. Feedback is always welcome.
- Lastly thank you Kunal Kushwaha and team ARMO for organising the security week. I learnt a lot during this week.
- Github Repository - github.com/kranurag7/kubescape-argo
Reference
- Rawkode Stream with Ben
- Devops Toolkit
- Saiyam Video on Argo
- ARMO youtube channel and Documentations
